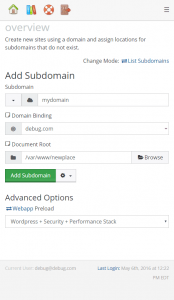
Effective immediately, one-clicks are gradually making their return to the control panel after an 8 year hiatus, but in a limited release on version 4.5+ platforms. Specifically, one-clicks are coming for WordPress, Drupal, Magento, and some basic Node/Ruby/Python scaffolding. Webapps may be managed within the control panel under Web > Web Apps or preloaded on subdomain/addon domain creation under the Advanced options dropdown.

Why now?
Simply noted, the control panel is now mature enough and provides enough internal functionality to support one-clicks in a coherent, optimized flow without nasty hacks. These one-clicks are also drastically different from what was once provided in the CP. These rely upon programs developed by the authors of the software to provide functionality. For WordPress there’s wp-cli, Drupal is drush, npm for Node, and gem for Ruby. No, this isn’t reinventing the wheel. It’s taking a perfectly fine wheel and putting it on a vehicle. This is how we are able to bring one-clicks back to the CP in limited capacity.
What about other apps?
These won’t be supported within the control panel until sufficient trust is established.
There is a lot to say about code quality. Why does an app crash? Bad coding. Why does an app have a security flaw? Oversight, bad coding. Why does an app become abandoned? Lack of dedication by the author, and your output is a product of your inputs, so let’s safely assume there is some bad coding involved in that decision making process. There are thousands of PHP applications out there. There are hundreds of Node and Ruby apps out there too, but they all lack a sufficient level of competency to safely and securely run. Having handled a couple dozen PHP7-specific adaptations for clients migrating to Luna, which uses PHP7 by default, I can say confidently that beauty runs skin deep. Often times, apps with less money behind them simply fail to attract necessary talent to produce software that works today and will continue to work tomorrow. Yes, some apps do some really stupid things, like use continue/break outside of loop structures (SimpleMachinesForum comes to mind as a repeat offender). PHP7 has clamped down on these mind-boggling incorrect uses of programming syntax.
Security is paramount, especially in an era where virtualization has enabled thousands more machines access to the Internet. These machines are often manned by unqualified personnel that remain neglected for so long only to succumb to third-party control through an exploit. Your hosting servers routinely block over 2,000 brute-force attacks per day. These blocks are based on egregious patterns (5+ logins within 3 minutes), but hundreds more fly under the radar trying only a handful of logins ever hour. Consequently, clients with weak passwords eventually fall victim to these drive-by hackings. It’s unfortunate. Clients are charged a service fee for cleanups. My time is often diverted, as an emergency, to clean up residual damage to ensure other clients conduct business uninterrupted. Moving forward, I want to continue to focus on building a secure platform. One-clicks help realize this vision through a few awesome components:
Fortification mode
Fortification mode is, by far, the most unique component to web apps deployed within the CP. Fortification bestows a secondary level of permissions through access control lists that permit mutual access by the web server, which runs as a separate user from your account. Before, this was accessible only by opening a ticket. Fortification allows the web server to write and modify files only to which it receives explicit authorization. In the event of a hack, a hacker can only modify files to which the web server has access. Beneficially, if a web site were hacked, the hacker is unable to access your email, SSH keys, and other confidential information. Fortification strikes a perfect balance between ease-of-use and security. Just toggle fortification via Web > Web Apps within the control panel. With fortification on, the web server cannot modify any files on your account. Comments and posts continue to post as normal. With fortification off, you may upload media to posts. Although, you’ll still need your control panel password to install new plugins!

Recovery mode
Circling back to a previous topic, crappy programmers beget crappy code. Recovery mode allows you to disable all third-party plugins and access a plain jane installation. Ideally, this will allow you to iteratively enable each plugin until you can safely determine which third-party programmer shouldn’t be a programmer.
Automatic updates
Coming soon. All one-clicks are enrolled into automatic updates to protect clients from zero-day exploits. These updates will roll out every night at 3 AM EDT during nightly CP updates. Tentatively, this will also extend to Ruby and Node.
Dual-user security
PHP apps run as a secondary user for myriad reasons. The most important reason is auditing; if an account gets hacked, we need to know what may be infected, what is infected, and what’s not. If the web server lacks write-privileges, then it is safe to say no. If the web server created the file within 24 hours of the incident, it’s safe to say yes. And if the web server had mutual write-access, then these require further auditing. Most hosting providers run PHP under your username, which is ludicrous, stupid, and irresponsible. It’s also the reason why major hosting providers bundle SiteLock service (which runs $100/mo plus a cleanup cost per infraction) service, their parent company owns UnitedWeb/IPOWER who in turn owns SiteLock, oh and their stock is (or was) doing very well! I base profit on providing a service, not holding clients who get hacked ransom. A $15 cleanup fee is charged to cover the 10 minutes it takes to do a quick audit and that’s it. We also scan uploads for malware, because once again we are in business to do good, not hold your account hostage due to negligence. In fact, the crux of this release is to make it impossible for you to be a victim. An online presence today is just as important, if not more important, than your physical presence; look at the power Yelp has to create or destroy businesses. Having a prospective client pull up a placeholder to the Syrian Electronic Army is a pretty damning display of incompetence. Look at the Panama Papers hack: outdated WordPress + single-user security. Let’s stop hacked sites. Let’s start by progressively providing secure platforms from the start.
Plugin stacks
WordPress comes with a couple stacks handpicked by my confidence to provide an uninterrupted and uneventful use of service. The security stack includes WordFence, renown for their investigative eye; XML pingback disabling; and comment disabling. The performance stack includes W3 Total Cache, which is used aggressively on the Knowledge Base and periodic database optimizations through WP Optimize. You can install both, either, or none depending upon what works best for your setup.
App enrollment
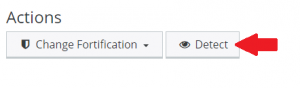
Got an existing WordPress app and want to enroll it into the new system? Easy as clicking Detect from within Web > Web Apps > Hostname selection. Got WordPress installed within a folder on your domain name? Click the dropdown menu and select Edit Subdir. Select your location from the filetree.
What’s next?
Drupal support through Drush is coming next (May 14 edit: Drupal is here), followed by Magento, which will include Let’s Encrypt support. We should see that sometime within the next week or so, followed by a lull as Passenger process management is planned for integration. Beyond this, I am always open to suggestions. Drop me an email at matt@apisnetworks.com with any idea whether big or small. After all, this control panel and platform wouldn’t exist without your voice!
Matt Saladna
Owner & Platform Developer
Updates
May 14, 2016: Drupal is now available
May 18, 2016: Magento 1.x is now available

Pingback:Updating WordPress - Apis Networks Knowledge Base
Pingback:Understanding Fortification - Apis Networks Knowledge Base